Using AWS Cognito with Google Authentication
Adding social authentication to your application should be pretty simple. And if you started with AWS Cognito, adding something like Google authentication is straightforward.
In this post, we will add Google authentication to an existing AWS Cognito User Pool.
To configure your Google identity provider, we will need Client ID, a Client Secret, and an authorization scope from your Google API account.
Go to https://console.cloud.google.com/apis/ to get these values.
Once there, click Credentials.
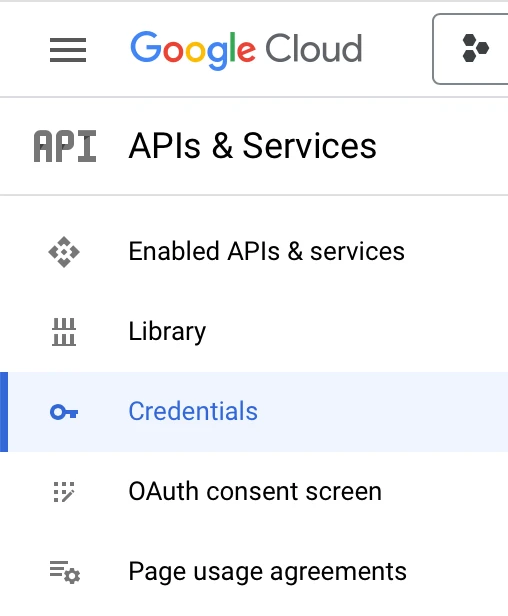
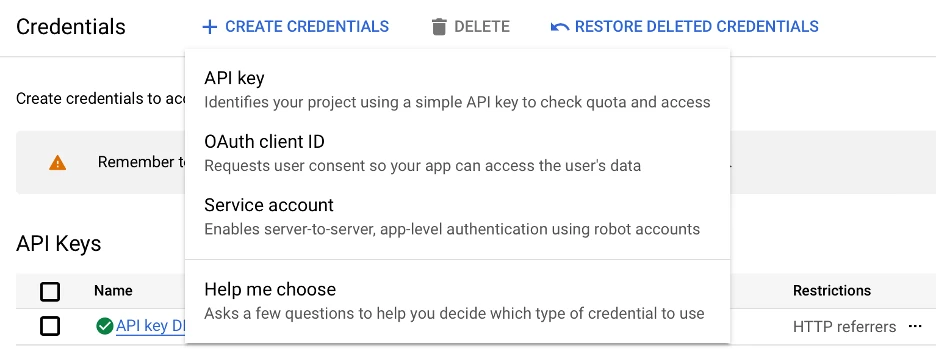
On the Credentials screen, click Create Credentials and then click OAuth client ID.
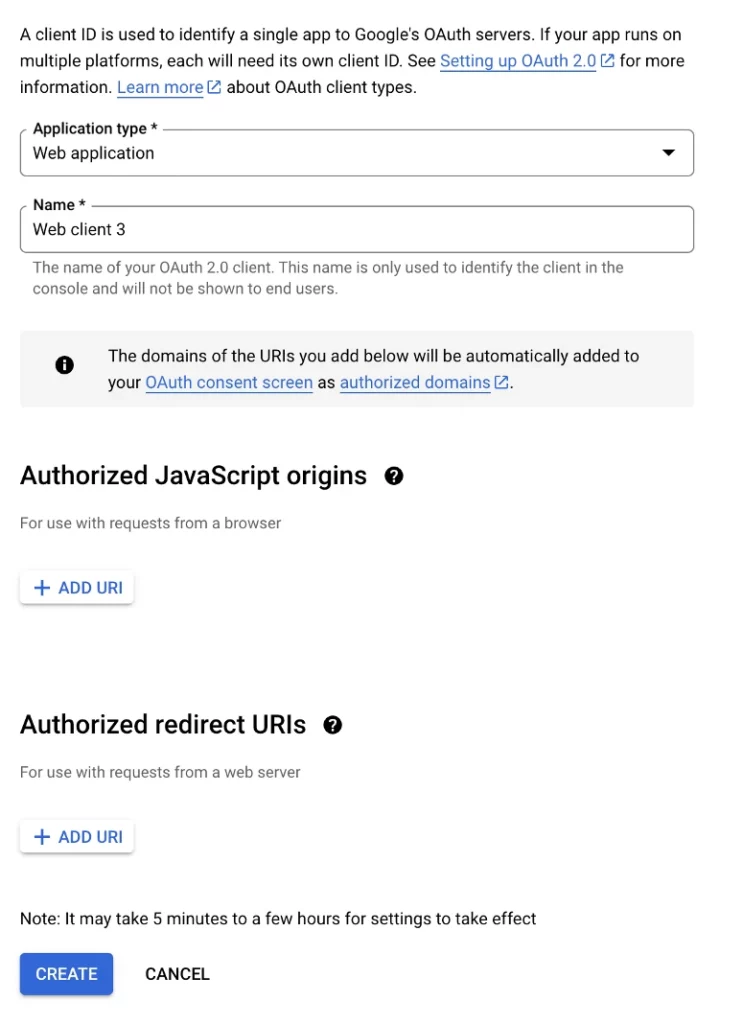
Select Web application as the Application type. You will need to add an Authorized redirect URI. This redirect URI needs to be the host name you use for Cognito, since Google will be redirecting back to Cognito.
Your URI should look like this: https://YOUR_COGNITO_NAME_HERE.auth.us-east-1.amazoncognito.com/oauth2/idpresponse
After you complete this screen, you will get access to a Client ID and your Client secret that you can copy into your Cognito User Pool setup screen.
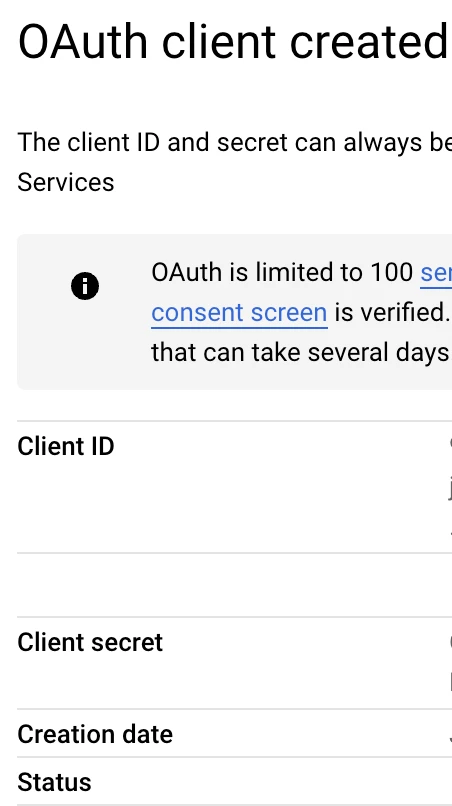
Log into AWS Cognito and navigate to “User Pools”.
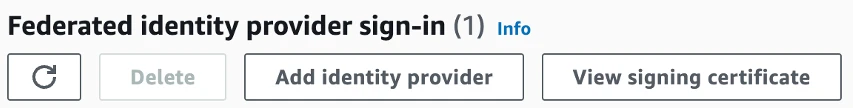
When you navigate to your user pool, go to the “Federated identify provider sign-in” and click the Add identity provider button.
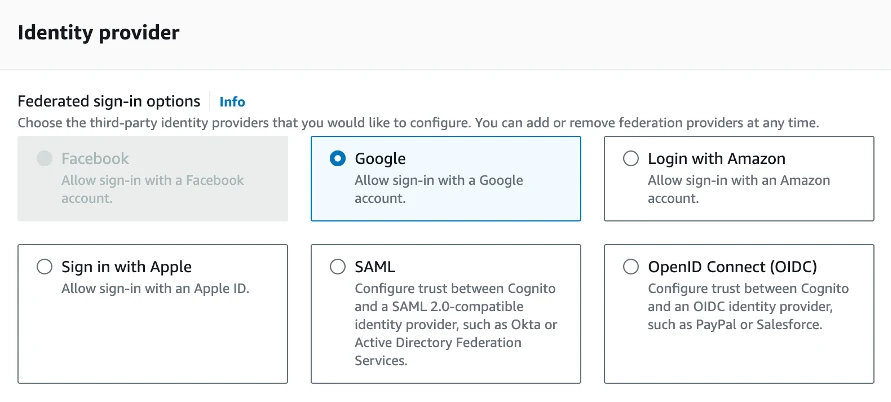
In the Identity provider section, select “Google”.
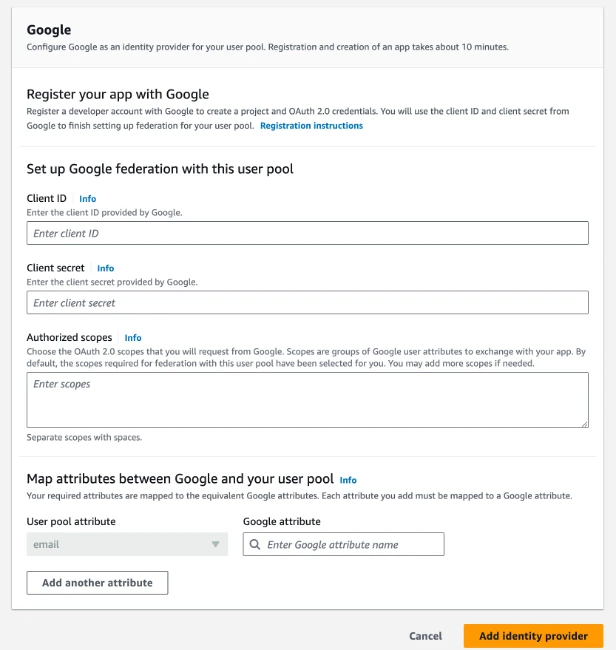
On the Google screen, enter the Client ID and Client secret from Google and then click Add identity provider.
Now you should be good to go. If you use my starter GitHub project (https://github.com/chadmichel/AuthStarter), you should be able to log in. Before using the starter GitHub project, you will have to configure your Cognito account to the starter project.

You should now see a “Continue with Google” option.
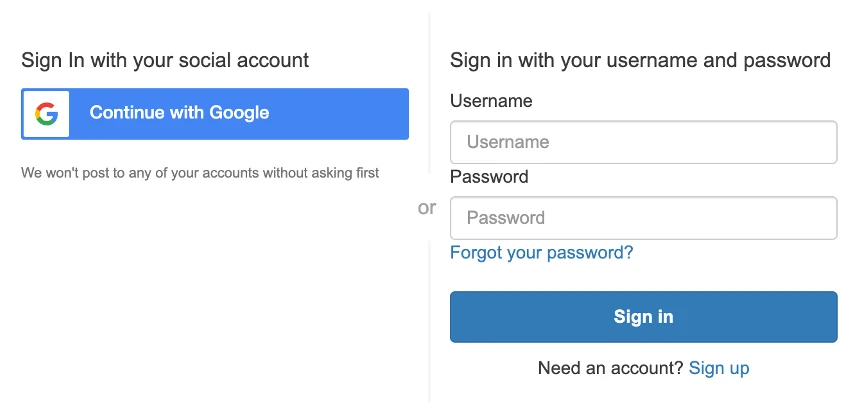
Or if on Mobile, you’ll see this:
Then you can enter your Google account details and sign in.