
Using an Access Control List to Block IP Addresses from Cognito
AWS Cognito is a very solid authentication service. We often use Cognito as an identity provider (IdP) for the applications we build. We redirect to Cognito, and then Cognito redirects back to us. Cognito gives us a code that we can use to get a JSON Web Token (JWT) to access our services. It’s a pretty standard Oauth workflow.
Cognito is a service that anyone can access. While this might be fine, we may want to implement specific rules. For example, we might want to block all non-US IP addresses or only allow a specific range of IP addresses.
In this blog post, we will set up an Access Control List (ACL) to block all non-US-based IPs.
First, go to your User Pool within Cognito in the AWS Console.
Navigate to the User Pool properties.
We need to create our ACL. In the ACL WAF area, click “Edit”.
You can use the existing ACL if you already have a web application firewall (WAF). But if you don’t have one, you must create one.
Click “Create Web ACL in AWS WAF”.

There are five easy steps to follow:
- Describe web ACL and associate it to AWS resources.
- Add rules and rule groups.
- Set rule priority.
- Configure metrics.
- Review and create web ACL.
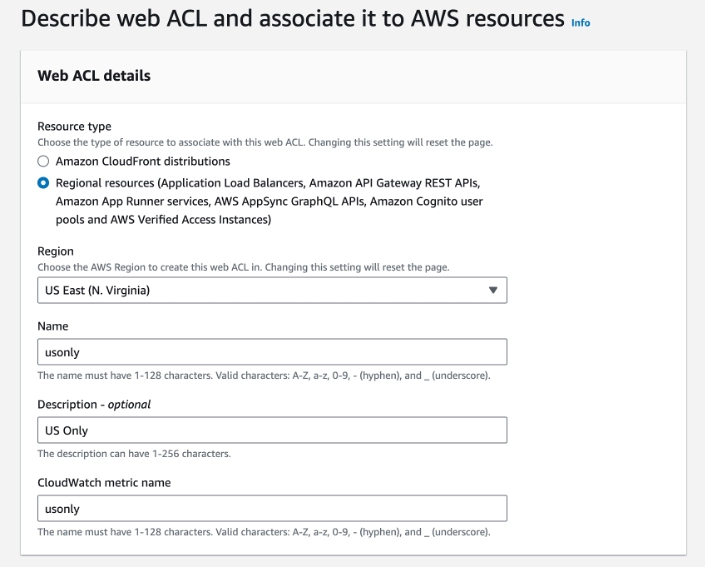
First, describe what your ACL does.
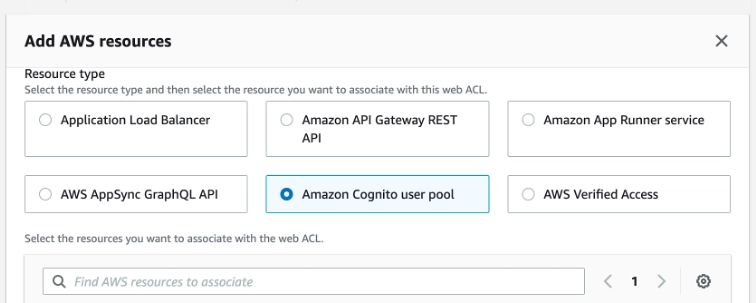
Then, add which resources will be using the ACL. For this example, we will select Amazon Cognito.
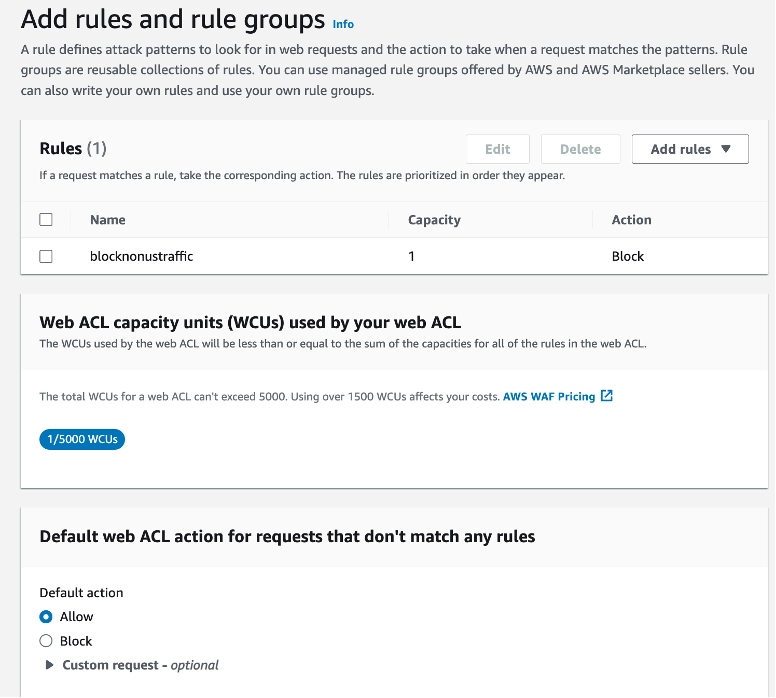
Then, we need to create the rules. In this case, we will create a rule that blocks all non-US IP addresses.
Then, we will set the rule priority. Since there is only one rule, this doesn’t matter for this example.
You can configure metric tracking to see if the rule has the desired behavior.
Now, AWS Cognito will only be available from US-based IP addresses. It would be easy to modify this demo to only allow from specific IP addresses, such as a specific office IP address.



