
Using AWS Cognito as an Identity Provider
AWS Cognito is an identity provider we can use to manage users in our systems. Cognito supports a simple oauth2 sign-in flow. Following this flow makes it pretty straightforward for users to sign in or sign up.
Before doing anything else, you must create an AWS Cognito user pool in the AWS Console.
For this example, we will use email-based authentication only.
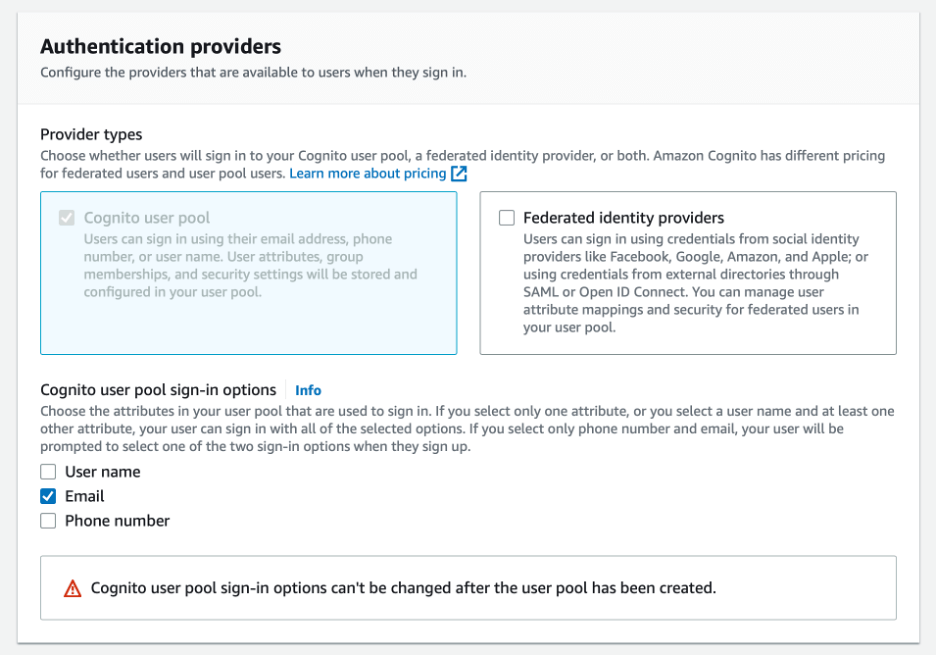
Next, we have to configure our security requirements. We can enable things like MFA (Multi-factor authentication) if we want.
We will also need to name our user pool.
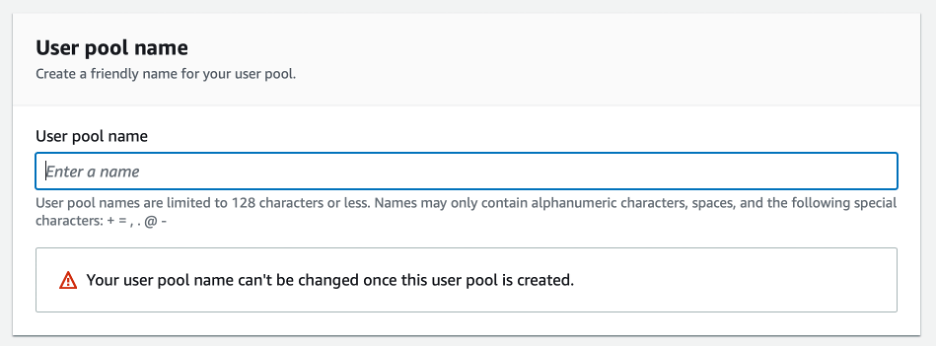
We will use Cognito’s hosted UI for this sample.
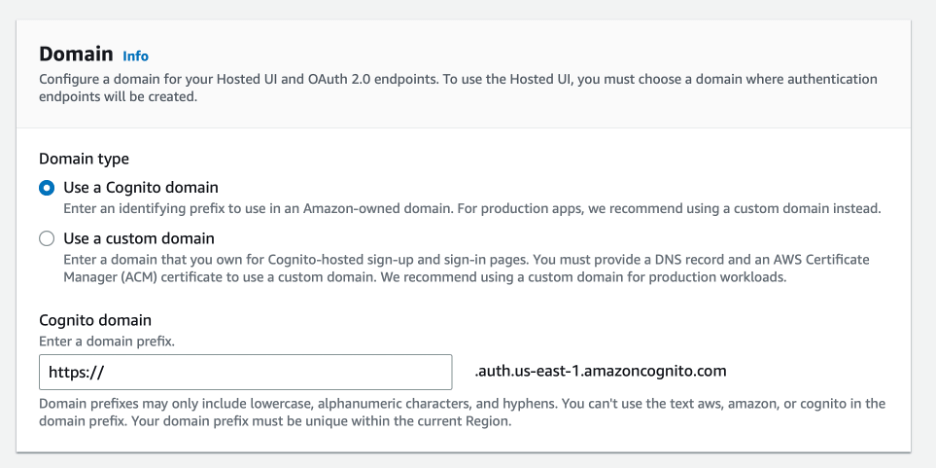
We will need to provide a domain name for the authentication client.
Once we have a Cognito user pool and client, we need to save a few values. The clientId and the client_secret for the client we created. Now you can authenticate your system against this new user pool.
How do you authenticate?
When you want to authenticate a user, you can redirect them to your Cognito URL. It will look something like this:
https://YOUR-DOMAIN.us-east-1.amazoncognito.com/login?client_id=YOUR-CLIENT-ID&response_type=code&scope=email+openid+phone&redirect_uri=YOUR_RETURN_URL.
At that URL, your user will sign in or sign up. Upon completion, they will be redirected to the URI you provided in the query string. Included in this redirection will be a code parameter in the query string. This code is something that can be used to retrieve a JWT. You should only do this JWT retrieval using your backend web server.
Overall, it’s a pretty simple setup process to use AWS Cognito as the identity provider for your application.
References
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-getting-started.html
https://docs.aws.amazon.com/cognito/latest/developerguide/tutorial-create-user-pool.html



